Security best practices for microservices architecture

Share This Article
Choose the best microservices vendor and trim the cost
Table of Contents
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.
Microservices are rapidly changing application development, and traditional monolithic architectures are being replaced with this new block in town. An O’Reilly Media mail list reader survey in 2020 found that approximately 92% of 1,502 respondents had experienced “some success” with microservices adopted by their organizations.
As this architecture model becomes more popular, the need for robust security increases. This is because there are more vulnerable points in microservices that are prone to security issues. In this blog, we attempt to provide a glimpse of the security challenges that microservices systems face and the latest strategies adopted to mitigate these challenges.
Common microservices security challenges
Organizations adopting the microservices architecture tend to face many security challenges. The challenges occur due to the fact that personnel manning the microservices are even now only learning the skills as the technology is relatively new. However, others tend to exploit the security vulnerability of the architecture.
Some of the microservices security challenges faced are:
- The complexity of the microservices architecture increases the possibility of more attacks
- The microservices in a system are built using different languages, frameworks, and technologies
- If the application has been scaled up, application security becomes a bigger challenge
- The microservices architecture has more service failures and other timeouts
Microservices - Security Strategies
As the microservices architecture continues to evolve, certain security practices and methodologies have combined to form broad strategies for implementing security in microservices. Here we discuss three such strategies.
- Defense-in-Depth Strategy
The defense-in-depth strategy is about implementing security at multiple layers to safeguard services that are sensitive. When implementing this strategy, the developer has to first identify the most critical of the services and then apply multiple layers of security.
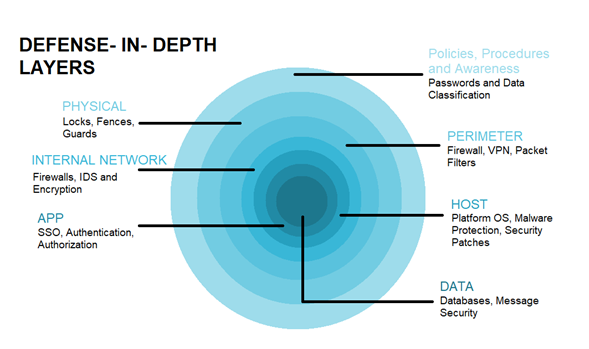
The figure shows the appearance of the defense-in-depth strategy when multiple layers of security are applied. It shows how the different layers of security protect the different resources and examples of security measures that are used for the implementation.
Read our blog, “Database Design in a Microservices Architecture”
As an example, if an attacker wants to access critical data, even if they manage to break the first outer layer, they will many more layers to breach to gain access.
- Isolation strategy
Isolation is one of the fundamental principles that is practised when building microservices architecture. Every service is isolated from other services and works independently. Isolating services in this manner minimizes the attack area if at all an attack occurs. Using API gateways, limited APIs, and encryption are recommended for the implementation of this strategy.
- DevSecOps strategy
DevSecOps is a practice that involves the development and operations team working closely with the security team with the goal of improving security. The primary goal of using DevSecOps is to secure every step in the pipeline. DevSecOps involves continuous monitoring, using automated code reviews, and setting up access security, amongst other related practices.
Download our eBook for free “MICROSERVICES- A Short Guide”
We believe in long-term win-win relationships with our strategic partners. If you want to migrate to microservices, call us today!
Some helpful tools and solutions include:
- Maven for Build, GitHub for SCM; Docker Registry can be used for image repository
- Honeybadger and LogDNA - continuous monitoring and logging
- xOps provides complete DevSecOps solutions for microservices security
Microservices security best practices
High-quality implementation of microservices security offers a great depth of protection. Multiple levels of security implementations are set up at each stage of development. It is recommended that organizations should apply the following practices when developing their microservices security strategy:
- Look out for dependencies
A dependency exists when one resource/part of the application relies on another. If you have used third-party code, this can bring external dependencies into the application. Tools such as GitHub’s Dependabot may be used to analyze source code and spot vulnerable dependencies.
- Make use of API gateways
As an application scales up, it is difficult to track individual APIs. In such a case, using API gateways makes tracking easier as it provides only a single entry point for all API-based communication.
- Implement monitoring at the services level
It is important to have both security tools as well as solutions that can monitor and protect the application at the service level to ensure security. Some monitoring tools used for the purpose include Sysdig, Prometheus, Trace, and Sensu.
- Use automation testing tools
Using automation is a good method of implementing security. A majority of security incidents are triggered off by misconfigurations and, therefore, in this context, it is a good idea to use automation testing tools. Some popular automation testing tools are:
- JMeter and K6 - performance testing
- Mocha and Jest - integration and unit testing
- Pact - contract testing
- Chaos Monkey - testing resiliency
These are some of the popular automation testing tools.
- Have strict identification and access control measures
Access control measures should be implemented at both the user and service levels. Given below are a few pointers for implementing access control:
OpenID for authentication (at user level)
- OAuth/OAuth2 for authorization
- Build a distributed firewall
- Use multi-factor authentication
- Using Mutual Transport Layer Security (mTLS) - mutual authentication between the microservices
- Implement network protection solutions
One of the major aspects that often gets neglected in microservices is securing the network. Functions such as communication between services, building, accessing applications, deployment, etc., everything uses some kind of network. Securing every communication line is critical to the secure functioning of the system.
- Avoid in-house encrypted code
Though encryption is good for security, in-house encryption are observed to be generally error-prone and can cause more damage than good. It is, therefore, advised to use standardized encryption protocols/tools unless your organization has personnel with a high degree of expertise available in security and cryptography.
Conclusion
If you are shifting to microservices, your requirement for better security increases. Your organization should be ready to prioritize and invest in microservices security. It is best to implement a combination of the best practices suggested above. This will enable the organizations to manage their microservices security successfully.
Do you want to deploy, manage, and scale up your mobile/on-premise/cloud microservices applications? Call us today!
Why Choose SayOne for Microservices Development
At SayOne, we offer independent and stable services that have separate development aspects as well as maintenance advantages. We build microservices specially suited for individuals' businesses in different industry verticals. In the longer term, this would allow your organization/business to enjoy a sizeable increase in both growth and efficiency. We create microservices as APIs with security and the application built in. We provide SDKs that allow for the automatic creation of microservices.
Our comprehensive services in microservices development for start-ups, SMBs, and enterprises start with extensive microservices feasibility analysis to provide our clients with the best services. We use powerful frameworks for our custom-built microservices for the different organizations. Our APIs are designed to enable fast iteration, easy deployment, and significantly less time to market. In short, our microservices are dexterous and resilient and deliver the security and reliability required for the different functions.
Share This Article
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.